No products in the cart.
Enterprise Cyber Security IT Risk & Security Management
Because Better Business Needs Assured Security.
WE ARE 100% COMMITTED TO SAFEGUARDING YOUR NETWORK, SYSTEMS, INFRASTRUCTURE AND DATA SECURITY

ABOUT US
Enterprises are moving their business processes towards digitization, mobility, big data analytics, web collaboration and cloud services. Most of them usually do not think of enterprise IT security strategy as a mandatory factor and lack adequate security experts on staff.
This, however, makes for a poor strategy that leads nowhere. Businesses should recognize enterprise IT security as their priority.Personal data, digital intellectual property, enterprise cyber infrastructure and even businesscritical apps can be compromised with network attacks, break-ins, inadvertent security lapses and vulnerable web services etc.
We’re providing a full range of IT relevant security Products & services. Our IT Security Products & Services offer businesses a deep, comprehensive overview of their vulnerability landscape in order to raise effectiveness in preventing advanced attacks and mitigate business risks.
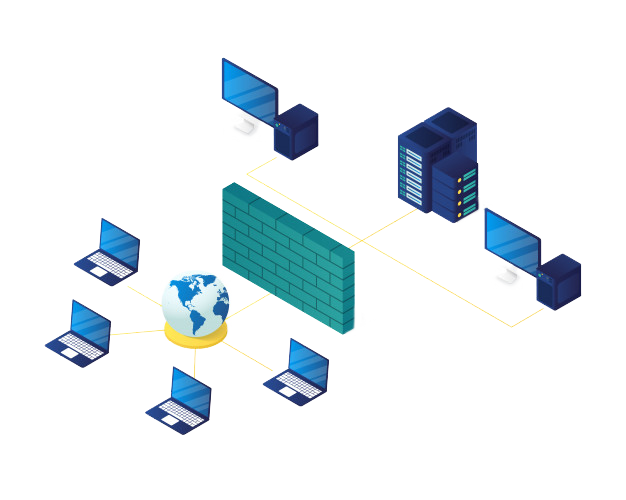
Managed Firewall Service
Managed Firewall Services from ESPL combines all of the products and services necessary to help you manage your network security needs & comply with industry standards at a fraction of cost of a full time security administrator.
Network security is a highly sought-after solution, at Envoque, we specialize in:
- Firewall Managment
- Intrusion Prevention System [IPS]
- Anti-Virus, Anti-Spam & Web Filtering
- Reporting
- VPN-Virtual Private Network [Work from Home Solutions]
Anti-Ransomeware Solution
We offer centrally managed cyber security for your office work station, Servers Remote Workers. Companies have paid
billions in ransom demands because their security let them down.

Don’t be the next victim.
Business Security in A Nut Shell:
- Made to protect small and medium sized businesses.
- Created by the world’s best ransomware experts.
- Super-fast and low on resource use.
- Multi-layered protection with next-gen technology.
- For workstations, servers and remote workplaces.
- Built with privacy in mind.
- Beautifully crafted for easy use.
- Making security management simple.
- Loved by customers all around the world.
Stop Ransomware. Before it encrypts your files.
- Signature-based detection
- Exploit detection
- Behaviour-based detection
- Ransomware-specific behaviour
EnterPrise Backup Solution

Data Loss & Breaches can be the worst nightmare for any Business, not being able to recover data in a timely manner will cost Time, Money and Resources.
Let’s be real — at some point, your business data is going to be at risk. The question to ask yourself is if your business can continue to operate at its required level without access to file data?
Your answer will likely vary based on the type of file data, and how old it is. Obviously, the older the data, the less critical it is to have short Recovery Time Objectives (RTO). However, what is an ideal RTO for your active data versus your archive data.
If you don’t have clear answers, or now how you’d recover in a disaster, it’s time to look at an enterprise backup solution.
Simply put, data is vulnerable. Business data can be lost due to a wide variety of reasons including
- Human error
- Machine error
- Viruses
- Natural disasters
You can never know at what moment your data may be at risk. In fact, 2020 was a record year for data breaches. Without a rocksolid backup plan, you may be facing a situation that can’t be recovered.
It’s time to make the move before it’s too late
Multi Factor Authentication
Data Loss & Breaches can be the worst nightmare for any Business, not being able to recover data
in a timely manner will cost Time, Money and Resources.
Black hat hackers’ biggest objective is to steal information for monetary gains. This is a major concern for all institutions today as they handle private information as well as finances. It is quite an easy task for an individual to capture usernames and passwords of other individuals by using multiple techniques like Sniffing, installing Key-logger.
Since 81% of cyber security breaches are due to stolen, weak or default passwords, multi-factor authentication (MFA) is very important for your authentication system. Implementing MFA, especially adaptive multi-factor identification, will help ensure security on all applications so you don’t have to worry about credentials being compromised and their information being stolen.
Implementing two-factor authentication will reduce the losses suffered by any institutions in terms of money and brand trust.
- Ease of integration and installation.
- Strong Authentication to prevent Identity Theft and other frauds.
- Regulatory Compliance
- Multiple Form Factors.
- Encryption and Privacy.
- Simple Administration.
- Competitive Costs.
You can never know at what moment your data may be at risk. In fact, 2020 was a record year for data breaches. Without a rocksolid backup plan, you may be facing a situation that can’t be recovered.
The Annual cost of Cyber-crime to Global Economy is more then 4 Million $$
E-Mail Security Gateway
The popularity of Office 365 means criminals test and design their attacks to bypass its native security features. And that means you need additional layers of defence. With Advanced Threat Protection enabled, E-Mail Security Gateway uses multiple layers of detection, including signature, static, and behavioural analysis, along with CPU-emulation sand-boxing to accurately detect and block zero-hour targeted attacks and ransomware.
.
Detect and Stop Account Takeover
Account takeover is one of the fastest-growing email security threats, and a complete email security strategy must offer protection against it. Protection from account takeover requires new technology that has visibility into internal email traffic. It detects and blocks most sophisticated email attacks that could lead to account takeover, and identifies behavioural and content-forwarding anomalies within already compromised accounts, to help you quickly identify and remediate against account takeover in real time. Native Office 365 defences are not able to provide this level of protection.
Protect your Office 365, G-Suite, any other Email Servers Solutions with E-Mail Security Gateway.
- Stops Advanced Threats.
- Stay Complaint & Productive.
- Keep your data safe.
- Stop Spam & Malware threats with inbound filtering
- Blocks advanced threats.
- Protects out bound email & stop Data Leaks.
- Protects remote workers from emering threats.

Cyber Security Collaboration With
Complete Peace of Mind









1
Step 1











